- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Security RenewalIf you have a computer, you should also have a reliable computer security application, but it should not be Windows Security Renewal. This application, or rather, infection, looks like legitimate antivirus software and attempts to persuade you to waste money on its so-called full version that will supposedly delete viruses and other infections. It cannot remove anything, because it is a clone of Windows Home Patron, Windows Virtual Firewall and other infections that attempt to swindle users out of their money in the same manner. Windows Security Renewal, as well as its “siblings” belongs to the Rogue.VirusDoctor family, which now consists of a great number of malicious applications. To scare the users into believing that he or she is infected, the malware produces scans that always show different infections. Do not remove them manually, because those infections do not exist in the system. What you should actually do is, first, ignore Windows Security Renewal, and then delete it from the system. Find some of the bogus messages that you should not trust: Error Error Error Besides simulated scans, infections and bogus messages, Windows Security Renewal impairs the system’s performance so that you cannot delete it easily. It disables the Internet, hides Task Manager and Registry Editor and blocks some executable files. Without these tools, you can remove Windows Security Renewal neither automatically, nor manually. Nonetheless, ethical hackers found the way to solve the problem. 0W000-000B0-00T00-E0020 is an activation key which you should copy and paste in an activation box and click on the Activate button. Once you register Windows Security Renewal, you can delete it from the system, because it does not display misleading information any longer and allows you to access the Internet and other Windows applications. However, if you do not want to use the activation key, you can still download a spyware removal tool and delete the infection automatically. Watch the video to learn how you can achieve this without activating the malware. We suggest that you remove Windows Security Renewal with a reputable antispyware tool, because this is by far the most convenient and the safest way to get rid of the infection. The malware’s components are located and deleted from the system so that new infections cannot be regenerated, which could happen if you attempt to remove Windows Security Renewal manually, because if you skip a file that is responsible for downloading malware, the system may be again infected.
Download Spyware Removal Tool to Remove* Windows Security Renewal
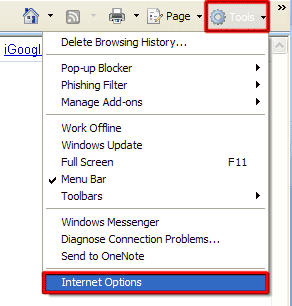
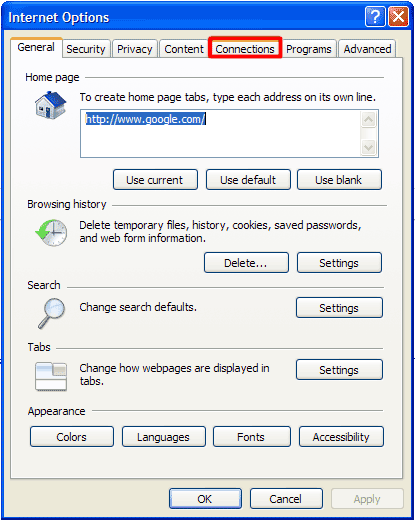
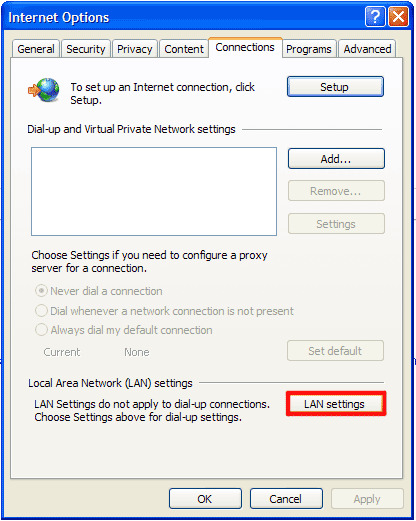
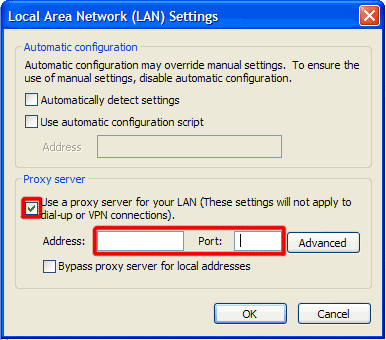
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Security Renewal
| ||||||||

|
How to manually remove Windows Security Renewal
Files associated with infection (Windows Security Renewal):
%CommonStartMenu%\Programs\Windows Home Patron.lnk
%AppData%\1st$0l3th1s.cnf
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Dynamic Link Libraries to remove (Windows Security Renewal):
Processes to kill (Windows Security Renewal):
Remove registry entries (Windows Security Renewal):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!