- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Web CombatThe Rogue.VirusDoctor family does not have its limits, because new rogues are produced almost every day. The latest release goes by the name of Windows Web Combat, which is also a clone of Windows Virtual Angel, Windows Profound Security, Windows Expert Series and other bogus security tools attributed to this same family. If you do not want to get bored while closing annoying bogus notifications and to face system disorders, remove Windows Web Combat from your computer at once. As Windows Web Combat is expected to be regarded as a legitimate antivirus program, its writers used Windows’ interface and the design to trick users into thinking that this application is reliable. Windows icons and colors of the logo are used in the interface; for instance, such icons as Home, Firewall or Quick Scan can be found in both Windows OS and the malware. As, presumably, you trust Windows, it is very easy to put one’s trust in this bogus application. Windows Web Combat scans your PC’s system and provides you with a list of imaginary infections. The infections that you find on the screen are not infections at all – they might be files of your system or files spread in there by the rogue. The files are renamed as infections so that you think that the system is heavily infected. Do not even think about a manual removal of those “infections” which, unfortunately, cannot be removed by Windows Web Combat, because you might delete wrong files. Moreover, you should pay no attention to the rogue’s intentions to lure you into believing the system is infected, which come to you in the form of simulated notifications. Find how those messages look like: Error Warning! Virus Detected Error To make the using of the computer troublesome, the rogue initiates various disorders which are expected to be so convincing that you finally decide to purchase the fake full version Windows Web Combat. The disorders are as follows: the Internet is disabled; Registry Editor and Task Manager are hidden, and certain executable files are paralyzed as soon as the user attempts to launch them. Do not think that the “full” version of Windows Web Combat will help you to get rid of infections. The malware, however convincing it might seem to be, cannot remove infection, because it cannot detected them, as well. As the only possible way to put an end to all of this is to delete Windows Web Combat from the system, do not hesitate to do it. We recommend you remove the malware with an antispyware tool, which you can download whenever your Internet connection is restored, which is done as soon as you activate the rogue with this key: 0W000-000B0-00T00-E0020 This way of removal is very convenient and safe, because the removal tool deletes only relevant elements and does not affect your system’s processing. Thus, if you really want to protect the system, remove Windows Web Combat automatically.
Download Spyware Removal Tool to Remove* Windows Web Combat
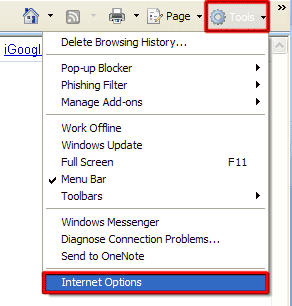
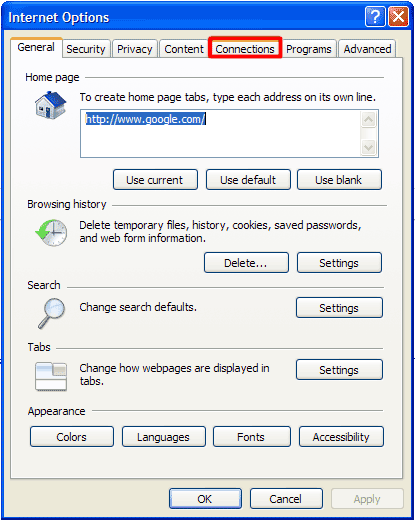
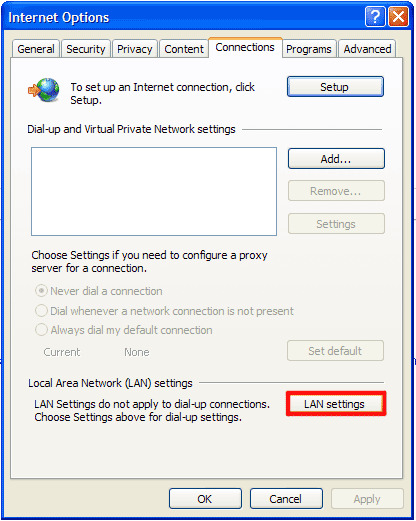
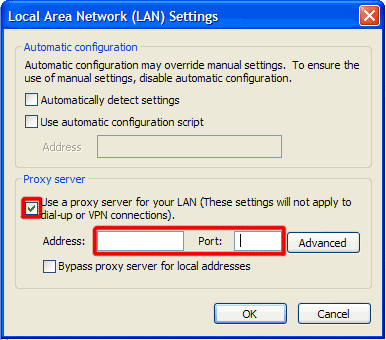
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Web Combat
| ||||||||

|
How to manually remove Windows Web Combat
Files associated with infection (Windows Web Combat):
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Web Combat.lnk
%Desktop%\Windows Web Combat.lnk
Dynamic Link Libraries to remove (Windows Web Combat):
Processes to kill (Windows Web Combat):
Remove registry entries (Windows Web Combat):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!