- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Instant ScannerWindows Instant Scanner is a cunning application which creeps into your computer’s system unnoticed. This malware is a product of the criminals who created Windows Custom Safety, Windows Privacy Module and other malicious and unwanted software. Windows Instant Scanner, as well as Windows Custom Safety etc, is attributed to Rogue.VirusDoctor family whose members share the same characteristics – they deceive people by using Windows applications interface, displaying misleading information and impairing the system’s processing to force you to pay money voluntarily for the so-called full version of the rogue. If you have this application on your computer, delete it, and tell your friend to do so if he or she has this infection on the computer. When you open the rogue, you see that the design of the tables is very similar or even identical to Windows applications. The same for colors of the icon – red, green, yellow and blue – are used on the interface of the rogue. Moreover, it is impossible to notice that the icons on the list of options on the left hand side are identical to the icons which you find when you open Start Menu. If you open Windows Defender, which comes with your OS, you will find that the icons at the top of the Windows Defender table are very similar to the icons of the rogue. Due to the appealing interface of the rogue, Windows users are easily fooled. Once users build up confidence in Windows Instant Scanner and install it into the system, the malware puts its plants into action. The rogue displays realistic scans and ends them by presenting a list of imaginary infections. Some of the infections may have names of real infections existing on the Internet. For example, Trojan.Win32.Qhost or P2P-Worm.Win32 might appear among the bogus infections. Do not attempt to remove those infections on your own, because these are just files named as actual infections. Moreover, the rogue tiresomely displays bogus notifications saying that a Trojan or a key logger has been detected. We highly recommend you ignore such information, because the malware, in general, does not present any correct information. Find how this infection might try to affect you and lure you into paying it for its imaginary full version: Error Error Error Ignore every single notification you get from the rogue. If you do what you are offered to do which is to active the rogue in order to remove infection, not only will you lose your money but also your sensitive data such as credit card or bank account numbers, log in passwords, etc. The cyber criminals that created this rogue want to get access to your money; therefore, do not make any money transfers related to the rogue but delete Windows Instant Scanner from the system. If might be difficult to remove Windows Instant Scanner, because it impairs the system so that its components cannot be detected and deleted. The malware hides Registry Editor and Task Manager, disables Internet connection and certain executable files. Registry Editor is hidden in order not to allow users to find registry entries created which should be deleted. Task Manager is necessary to check the processes of the system, and without this tool, users cannot view what processes related to the rogue are active. The Internet connection and executable files are disabled for the same reason. Without Internet connection you cannot download a removal tool, whereas without certain executable files you cannot launch system scans to detect infections. However complicated the situation might seem to be, there are two ways to eliminate the infection. The first way of removal of the rogue is manual removal. To delete the rogue manually you have to restore the tools which are disabled. To restore those applications, activate the rogue with the activation key provided: 0W000-000B0-00T00-E0020 Remove the components of Windows Instant Scanner completely, because if something related to rogue is left in the system, there is a high risk that the system will be infected again. To avoid this, we recommend you remove Windows Instant Scanner automatically, which means that you have to use a legitimate antispyware tool which is able to eliminate this infection. The rogue will be deleted, and, at the same time, the system will be protected against further infections.
Download Spyware Removal Tool to Remove* Windows Instant Scanner
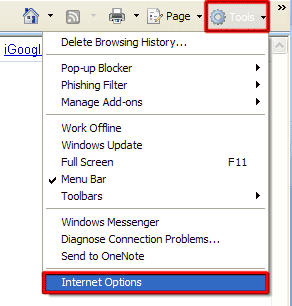
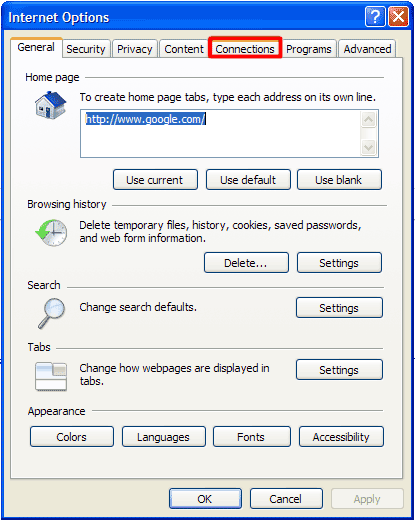
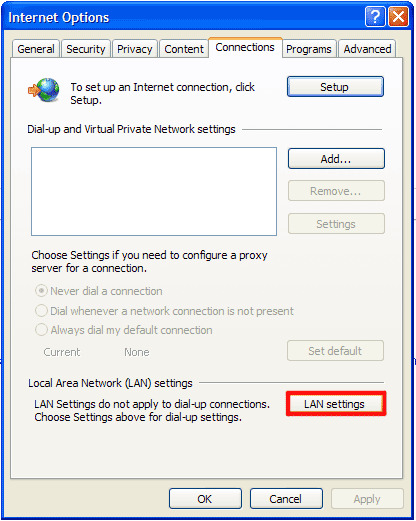
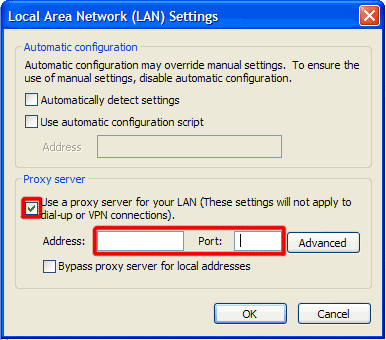
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Instant Scanner
| ||||||||

|
How to manually remove Windows Instant Scanner
Files associated with infection (Windows Instant Scanner):
%CommonStartMenu%\Programs\Windows Custom Safety.lnk
%AppData%\1st$0l3th1s.cnf
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Dynamic Link Libraries to remove (Windows Instant Scanner):
Processes to kill (Windows Instant Scanner):
Remove registry entries (Windows Instant Scanner):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!