- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
- Shows commercial adverts
Windows Custom SafetyHaving Windows Custom Safety on the computer is not the best choice because this is a cunning program designed to mislead you into believing in the vulnerability of the system. The rogue will offer you to activate it to have “ultimate protection” of the system. Do not believe a word of the rogue and remove it from the system. At the beginning, you might think that Windows Custom Safety is a very useful application, because it scans the system, however the scans are simulated, and you should not trust the results of the scans. The rogue provides you with a table of bogus threats such as viruses, Trojans and malware. Interestingly, Windows Custom Safety cannot remove these “infections” for free. According to Windows Custom Safety, if you want to remove those supposedly real infections, you have to purchase the full version. Please do not trust Windows Custom Safety, because your money is what the cyber criminals behind this rogue are dreaming of and delete this malware and protect the system. The easiest way to get rid of Windows Custom Safety is to remove it by using a legitimate antispyware tool. All that you need is to install a powerful tool which will kill the infection at once and not cause damage to the system. Windows Custom Safety will be removed completely, because only the files of the infection are eliminated by antispyware. If you try to delete Windows Custom Safety manually, you might delete files which are necessary for the system to function properly. Thus, get rid of Windows Custom Safety automatically and use your PC as usual. UPDATEWindows Custom Safety derives from the Rogue.VirusDoctor group of rogue antispywares, and Windows Privacy Module, Windows Maintenance Suite and Windows PC Aid are only a few clones of the newly distributed rogue. All of the viruses in this family were made to resemble legitimate Windows programs, so if you notice familiar controls or layouts, be sure that it is just an illusion, and you should hurry up to delete the rogue! Unfortunately, this task will be aggravated by removed controls over the Internet, Registry Editor, Task Manager and running of most executables, which is why before you delete the rogue, you should get rid of these symptoms. To restore Internet connection, below you will find connection renewal instructions, and to remove other symptoms, you can use this registration key: 0W000-000B0-00T00-E0020 This will also help you remove such bogus security notifications: Warning! Spambot detected! Warning Error
Download Spyware Removal Tool to Remove* Windows Custom Safety
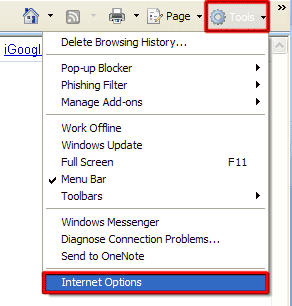
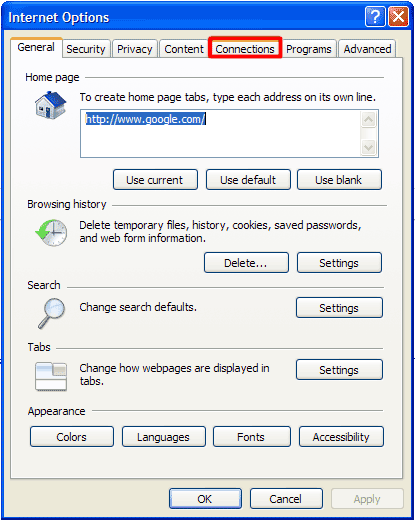
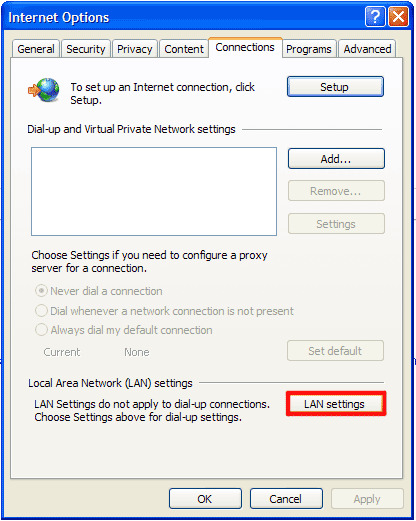
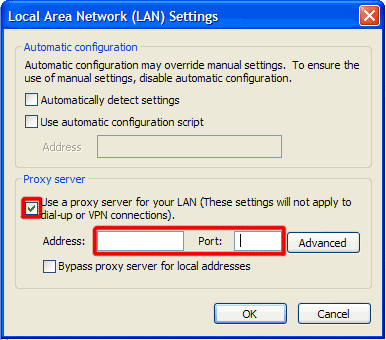
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Custom Safety
| ||||||||

|
How to manually remove Windows Custom Safety
Files associated with infection (Windows Custom Safety):
Protector-byrm.exe
Protector-oofi.exe
Protector-aayq.exe
%AppData%\NPSWF32.dll
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Custom Safety.lnk
%Desktop%\Windows Custom Safety.lnk
Dynamic Link Libraries to remove (Windows Custom Safety):
Processes to kill (Windows Custom Safety):
Protector-oofi.exe
Protector-aayq.exe
%AppData%\Protector-[Random].exe
Remove registry entries (Windows Custom Safety):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!