- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Maintenance SuiteWindows Maintenance Suite might give you a headache if you believe what it tells you. Remove this simulated security application as soon as it appears on the screen. The application is a clone of Windows PC Aid and Windows Safety Wizard which belong to Rogue.VirusDoctor family. The malware is created to trick you into thinking that you have caught a bunch of various infections. Windows Maintenance Suite will offer to acquire its fake full version to remove the infections that are presented as very dangerous. Windows Maintenance Suite will produce various infections to scare you. The system is supposedly scanned, and bogus infections are presented on the screen. You might find such threats as Trojan-Downloader.Win32.Agen, Backdoor.Win32.Rbot, P2P-Worm.Win32 and others. You should not try to delete these infections because they do not exist on your computer. If you attempt to remove them, you might delete files which are relevant to the functionality of the system. Remove Windows Maintenance Suite, instead of damaging your computer, and then find a way to protect the system against such a real infection as P2P-Worm.Win32 and others. Additionally, you should ignore information presented by Windows Maintenance Suite. The malware displays annoying pop-up messages such as errors or warnings, which are difficult to get rid of. Do not trust their content – there is nothing real about them. Some notifications are listed below: Error Warning! Virus Detected Error Windows Maintenance Suite is also capable of impairing functionality of the system which strengthens the impression that the system is infected and that certain damage has been done. For example, disablement of your Internet connection is the most noticeable impairment which is done to prevent the removal of the rogue. Furthermore, the malware hides Registry Editor and Task Manager as well as some certain executable files which could detect the infection. The disorders can be fixed if you activate the rogue. The activation key which is acquired after the purchase of the full version of Windows Maintenance Suite is already provided, and you do not have to spend your money on the activation. Activation key: 0W000-000B0-00T00-E0020 Having activated the rogue, you have to eliminate the infection. The malware quiets and you can remove the rogue undisturbed by pop-ups messages and errors. You have to delete the constituents of the rogue so that the infection cannot recover. Do not leave a single element of the malware, because the removal of Windows Maintenance Suite will be useless if you miss anything. If it is too hard to delete the rogue manually, you can get rid of it by using antimalware. It is better to invest money in the system’s protection than spend money on imaginary application. Use a powerful and reliable antimalware tool which is able to remove Windows Maintenance Suite, and you will not have to do anything, because the components of the rogue will be removed for you automatically.
Download Spyware Removal Tool to Remove* Windows Maintenance Suite
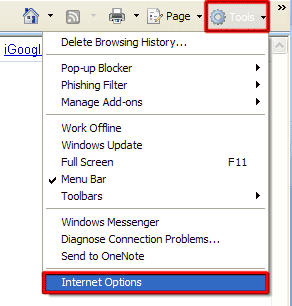
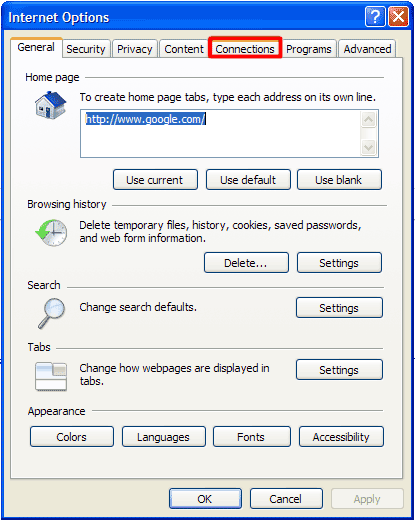
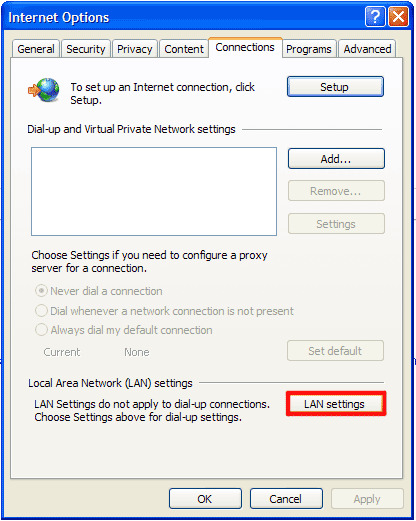
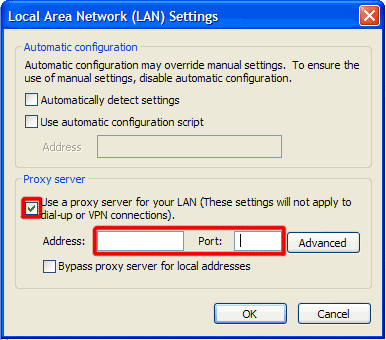
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Maintenance Suite
| ||||||||

|
How to manually remove Windows Maintenance Suite
Files associated with infection (Windows Maintenance Suite):
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows Maintenance Suite.lnk
%Desktop%\Windows Maintenance Suite.lnk
Dynamic Link Libraries to remove (Windows Maintenance Suite):
Processes to kill (Windows Maintenance Suite):
Remove registry entries (Windows Maintenance Suite):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "otbpxlqhjd"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!