- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows PC AidWindows PC Aid belongs to the Rogue.VirusDoctor group, which has been active since 2009, and for the past three years, such clones as Windows Malware Firewall, Windows Antivirus Rampart or Windows Functionality Checker have entrenched upon security of thousands of Windows OS users. The infection exceptionally attacks those computers with poor level protection, and so all Windows owners should keep their antimalware software updated, because only such tools could remove Windows PC Aid or, in the first place, guard against its entering. The malignant application has been witnessed to travel via encrypted downloads, black hat SEO scams, and other latent infections, but you should be extra careful of fake online scanners. Such implementation could trick you into downloading infection’s setup, which would initiate all malignant processes! Once in, the dangerous cyber criminals’ tool will make you panic about your system’s security, and various system infections, which will be reported by the fake computer scanner. If not enough, tons of bogus security notifications will flood the screen until all of your resistance is shattered! Here is some of the fake alerts you might come across: Recommended: Error These bogus warnings will keep rushing you to purchase full version of Windows PC Aid to remove the completely fictitious infections, but you should be also aware of other dangerous malignant application’s symptoms. Be sure that blocked Internet connection, removed access to Registry Editor and Task Manager, or inability to run high-importance executables are just simulated malfunctions, created to make it impossible for you to detect and delete Windows PC Aid. You should not believe the hazardousness of the symptoms, because if you do, you might get tempted by Windows PC Aid removal tool, included in rogue’s licensed version! Do not waste your $99.90 on something so useless, and install a security tool, which could be capable to detect and remove real computer hazards. To start removal processes, you should start by registering an activation code, which would be able to remove Windows PC Aid’s symptoms, or by renewing Internet connection with given instructions. Only this way your system will be freed from paralyzing dysfunctions, and you will be able to delete the rogue from your system. Of course, if you do not want to use the code, you can also transfer downloaded antimalware installation files onto the infected PC from a healthy system; however, no once can tell whether those files could be launched, because of the removed control over most system’s executables. Windows PC Aid removal alleviating activation code: 0W000-000B0-00T00-E0020
Download Spyware Removal Tool to Remove* Windows PC Aid
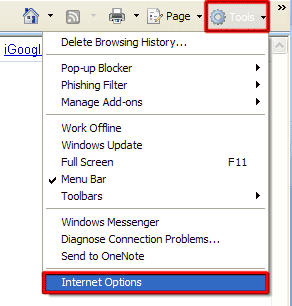
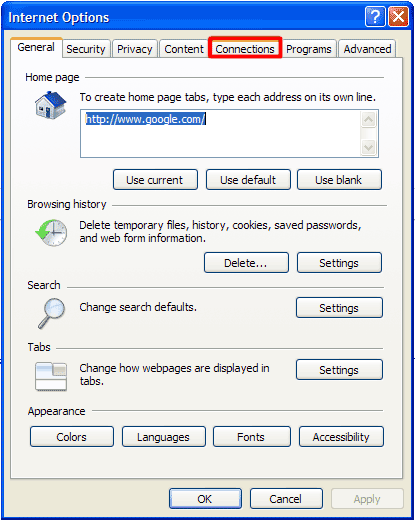
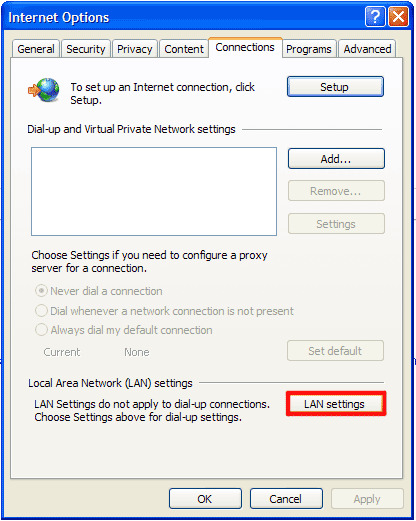
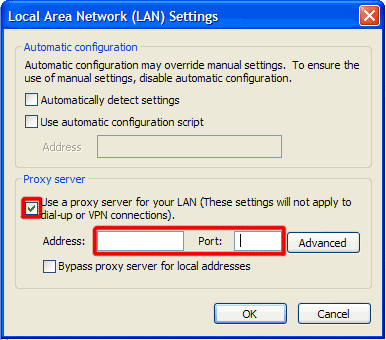
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows PC Aid
| ||||||||

|
How to manually remove Windows PC Aid
Files associated with infection (Windows PC Aid):
%AppData%\Protector-[Random].exe
%AppData%\result.db
%AppData%\1st$0l3th1s.cnf
%CommonStartMenu%\Programs\Windows PC Aid.lnk
%Desktop%\Windows PC Aid.lnk
Dynamic Link Libraries to remove (Windows PC Aid):
Processes to kill (Windows PC Aid):
Remove registry entries (Windows PC Aid):
HKEY_CURRENT_USER\Software\Microsoft\W
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[1].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npfmessenger.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsadbot.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe

Post comment — WE NEED YOUR OPINION!