- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Antivirus RampartMalware like Windows Antivirus Rampart should be removed from your computer the moment you notice that its computer scanner is running in your operating Windows system, because all that this Rogue.VirusDoctor family rogue (clone: Windows Ultimate Security Patch) represents is completely fictitious and should not be trusted one bit! Actually, what you should do right away, is copy a registration key, which you can see bellow, and use it to remove Windows Antivirus Rampart virus symptoms, which could seriously compromise your computer and endanger your private data! Registration key: To activate the registration key, which will allow you to remove the dangerous infection, should be entered in to the registration filed, found in the rogue’s purchase page. This way, you will trick the deceitful application that you have spent your money on Windows Antivirus Rampart’s full version. In reality, you should not even consider spending your money on the bogus security program; however, the researched key will free your system from paralyzing dysfunctions, including such bogus security notifications, constantly reminding that you should remove malicious infections, reported by the fake virus’ computer scanner. Error Recommended: Recommended: Nonetheless, these bogus pop-up warnings are not the dysfunctions you should be most careful of, as Windows privileges to access Registry Editor and Task Manager will be removed, and running of most important Windows executables will be blocked. These attributes of your system are most essential, if you are thinking about having Windows Antivirus Rampart deleted manually, or installing automatic removal tools, which could do it for you. Even more, Internet connection will be blocked, leaving you without any access to research the dangerous applications, which is the exact intention of schemers, who will try to push the rogue’s licensed version through as the most reliable removal tool. Without one doubt, you should act responsibly and delete Windows Antivirus Rampart from your computer at once, and automatic removal tools will work best in your Windows system. And remember, malware gets in through unprotected security cracks, which can only be monitored and protected by full-time, legitimate applications.
Download Spyware Removal Tool to Remove* Windows Antivirus Rampart
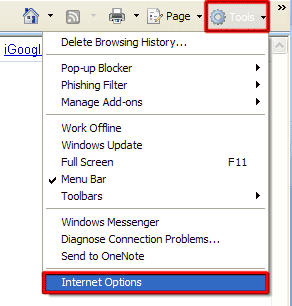
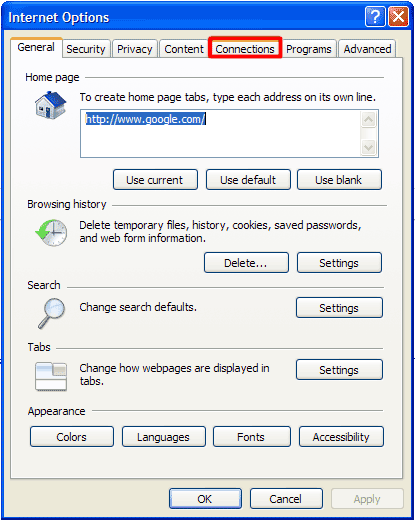
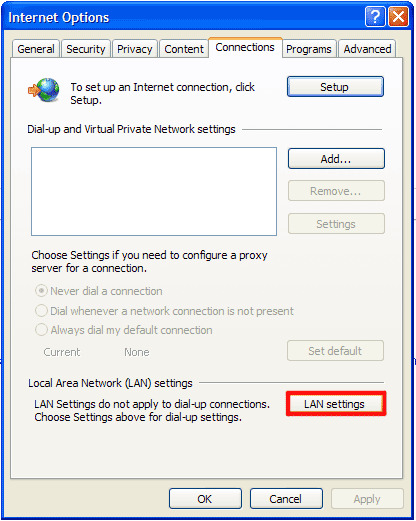
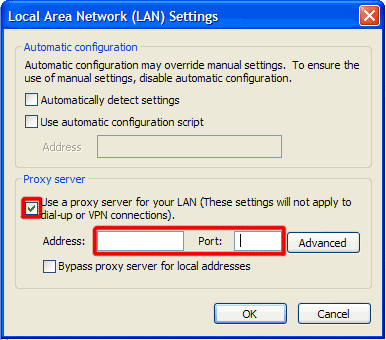
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Antivirus Rampart
| ||||||||

|
How to manually remove Windows Antivirus Rampart
Files associated with infection (Windows Antivirus Rampart):
%CommonStartMenu%\Programs\Windows Antivirus Rampart.lnk
%AppData%\1st$0l3th1s.cnf
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Dynamic Link Libraries to remove (Windows Antivirus Rampart):
Processes to kill (Windows Antivirus Rampart):
Remove registry entries (Windows Antivirus Rampart):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-29_7"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "yurrockari"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntiVirus_Pro.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brasil.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hbinst.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mu0311ad.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\purge.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0

Post comment — WE NEED YOUR OPINION!