- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Annoying Pop-up's
- Slow Computer
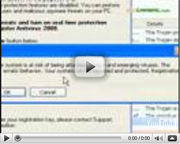
Windows Guard ToolsThe cyber criminals, who created Windows Multi Control System, have released Windows Guard Tools. The rogues are members of the Rogue.VirusDoctor family which also includes such fraudulent applications as Windows Pro Safety, Windows Private Shield and others. The rogue employs a variety of ways to deceive the PC user into revealing such banking data as credit card number, passwords or CVV/CVC2. The rogue pretends to be a security application which supposedly detects infections and removes them after the activation of the full version. If you find this or similar application saying that the infections will be removed once the full version is registered, delete the application and ensure that the computer’s system is protected. Before asking you to conduct an online money transaction, the malware will produce fake scans of the system, threats, and pop-ups. You will be enlightened about the harm of the system made by such imaginary infection as Trojans, rootkits or various malware. Do not try to remove those infections on your own, because you might delete valid files of the system. Please find some bogus notification to see how Windows Guard Tools might trick you into believing that the system is full of infections: Error Error In addition to the false information, Windows Guard Tools simulates Windows settings. For example, the Firewall, Automatic updates and Antivirus protection options are shown OFF, and the rogue suggests users follow its recommendations to protect the computer even though the actual settings might be ON. In addition, the rogue disables the Internet connection to stop users from finding out what Windows Guard Tools really is and from removing the rogue from the system. Task Manager and Registry Editor are also disables so that users can not examine the processes of the system and remove the registry entries created by Windows Guard Tools. The malware also blocks executable files that are responsible for the maintenance of the system’s security; therefore, whenever the users want to run the system’s scan, the security application might be blocked. These malfunctions of the system are restored after the registration of the rogue by entering a registration key. Do not pay money for the key, because it is provided for you: 0W000-000B0-00T00-E0020 Once you enter the key, you can delete Windows Guard Tools manually. Find and remove all the components of the rogue in order to terminate the infection. If you leave a file of the rogue undeleted, there is a risk that the infection will be renewed or another infection will be installed. If you are not confident enough about your abilities to remove Windows Guard Tools on your own, our recommendation is that you use a reliable antispyware program. The antispyware tool does not damage the system, because it deletes only the rogue-related files; moreover, it ensures protection against future infections.
Download Spyware Removal Tool to Remove* Windows Guard Tools
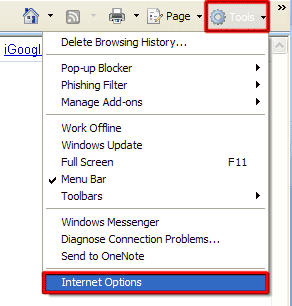
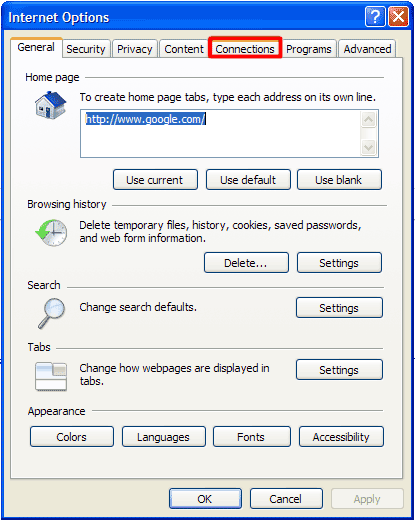
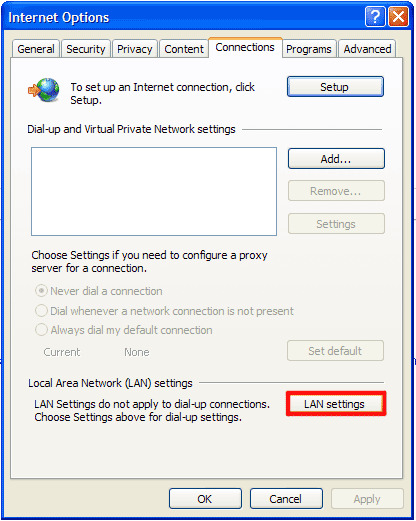
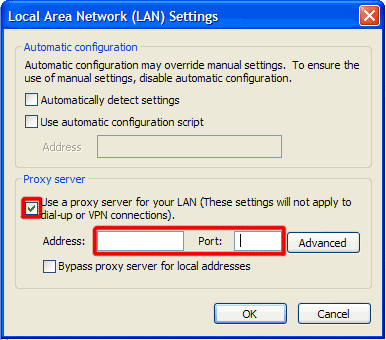
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Guard Tools
| ||||||||

|
How to manually remove Windows Guard Tools
Files associated with infection (Windows Guard Tools):
%AppData%\result.db
%AppData%\Protector-[Random].exe
%StartMenu%\Programs\Windows Guard Tools.lnk
Dynamic Link Libraries to remove (Windows Guard Tools):
Processes to kill (Windows Guard Tools):
Remove registry entries (Windows Guard Tools):
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavastsvc.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavastui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsegui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsekrn.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsascui.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsmpeng.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmsseces.exe "Debugger" = 'svchost.exe'
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionSystemRestore "DisableSR " = '1'

Post comment — WE NEED YOUR OPINION!