- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Pro Safety ReleaseWindows Pro Safety Release virus is the newest addition to the shockingly vast Rogue.VirusDoctor family of fictitious antispyware tools, which does not have the technical potential to delete computer threats, or guard your PC against them, like a real antispyware could. However, the fake tool does not even need these attributes, as cyber criminals rely heavily on its interface to create successful and profitable scam attacks on oblivious Windows users. If you think it will be easy to remove Windows Pro Safety Release, keep reading to find out all that this treacherous security tool is capable of. If your operating Windows system is not protected by legitimate safeguard applications, Windows Pro Safety Release or any of its clones (Windows Safeguard Upgrade, Windows Pro Solutions, et al.) could infiltrate your system at any point! Hackers, who work behind Rogue.VirusDoctor family, are experienced at detecting the simplest security loopholes that can be used for attacks. Such backdoors include encrypted downloads, fake online scanners, disguised infection’s setups in spam email attachments, or any other sources that no one could suspect. Once inside a system, Windows Pro Safety Release lures its victims as a helpful computer scanner, which detects tens of bogus threats and tries to pass them as real. Such ridiculous proclamations also get complemented by many deceitful security notifications, imitating ones of Firewall and Windows Security Center. To top it of, most essential attributes, required to delete Windows Pro Safety Release virus, will be compromised, as Internet connection and running of most executables will be blocked, and access to Task Manager or Registry Editor will be removed. This way you will be paralyzed, without a way to research the rogue or remove it swiftly. Nonetheless, whatever you do, it is a must to ignore any virus’ full version purchase recommendations, as this is the goal of virtual schemers’ sinister plan! See a few of them: Recommended: Error Recommended: To regain Internet connection use out renewal instructions, and to remove these cunning alerts and other symptoms, we advise using an activation code, which will do the job. Activation code: 0W000-000B0-00T00-E0020 Once the infection is controlled, all you will be left to do is remove Windows Pro Safety Release from your computer. Even though manual removal is applicable to this rogue, we strongly recommend installing legal security tools, which would save you time when having the virus deleted, and which protect Windows OS for months to come.
Download Spyware Removal Tool to Remove* Windows Pro Safety Release
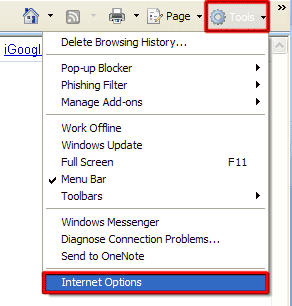
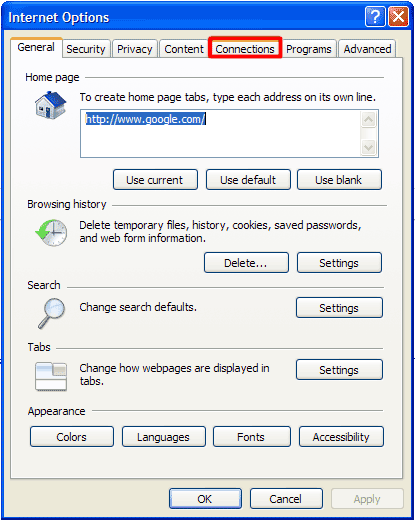
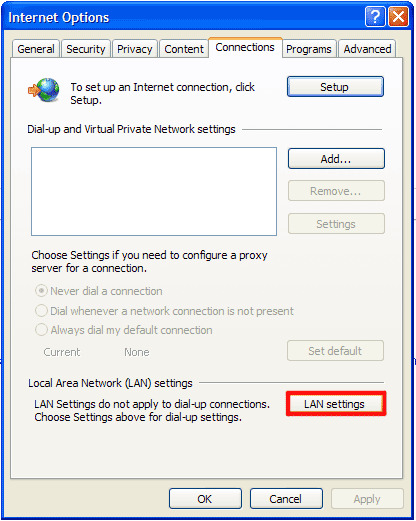
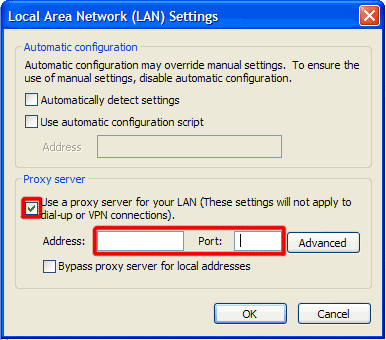
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Pro Safety Release
| ||||||||

|
How to manually remove Windows Pro Safety Release
Files associated with infection (Windows Pro Safety Release):
%CommonStartMenu%\Programs\Windows Pro Safety Release.lnk
%AppData%\NPSWF32.dll
%AppData%\Protector-[Random].exe
%AppData%\W34r34mt5h21ef.dat
%AppData%\result.db
Dynamic Link Libraries to remove (Windows Pro Safety Release):
Processes to kill (Windows Pro Safety Release):
Remove registry entries (Windows Pro Safety Release):
HKEY_CURRENT_USER\Software\Microsoft\Win
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-6_2"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "ungklgkqft"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iface.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\netspyhunter-1.2.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rscdwld.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tcm.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winstart.exe

Post comment — WE NEED YOUR OPINION!