- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Shows commercial adverts
- Annoying Pop-up's
- Slow Computer
Windows Recovery SeriesWindows Recovery Series is a Windows compatible tool, which will proclaim capability to remove system corrupting malware. If you believe this, you will be shocked to find out that your operating system is not being attacked by vicious malware you need to delete, and that Windows Recovery Series is just a clone of widely known fake antispywares Windows Safety Checkpoint, Windows Premium Guard, etc. Windows Recovery Series’ creators are only after your money, and to reach this, you will have removed privileges to control your system’s processes via Windows Tools (Registry Editor, Task Manager), stopped from connecting to the Internet or launching most Windows executables. Overall, if you do not remove Windows Recovery Series, this rogue can cause ever greater damage to your personal security! Hackers, taking care of Windows Recovery Series’ infiltration, are well experienced with the previous application’s clones, so they know every single Windows security backdoor, which could be used to slither Windows Recovery Series in unexpectedly. And even though most rogue’s victims may not understand where Windows Recovery Series comes from, they still are known to trust this bogus security tool, because of its well crafted interface. It is mostly because application’s windows appear to look very similar to the regular Windows OS programs. All of the management tabs are positioned left, and even the color scheme replicates the one of Windows tools. It will also be hard not to trust Windows Recovery Series, because of the constantly flooding security notifications: Recommended: Error Error All Windows Recovery Series’ removal recommendations are meant to bait you to purchase completely ineffective rogue’s full version, purportedly equipped to delete counterfeit infections. Obviously, these bogus Windows Recovery Series alerts and other dysfunctions must be removed in order to regain Windows’ control. One of the ways to do so is to apply the activation key bellow: 0W000-000B0-00T00-E0020 Without a doubt, Windows Recovery Series must be removed! And there are two ways to accomplish that: manual and automatic. Manual removal will be an easy nut to crack for experienced Windows experts, familiar with the task, but majority users should leave it to the legitimate security applications to delete Windows Recovery Series. So, do not hesitate and remove this fake tool without waiting any minute longer. Note: to install security software, which will remove Windows Recovery Series, use our Internet connection renewal instructions!
Download Spyware Removal Tool to Remove* Windows Recovery Series
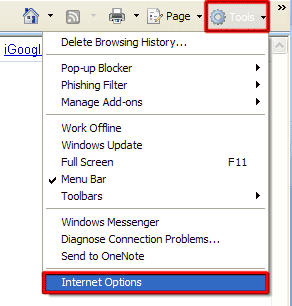
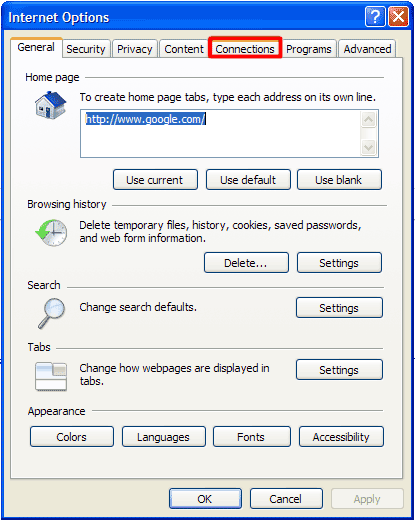
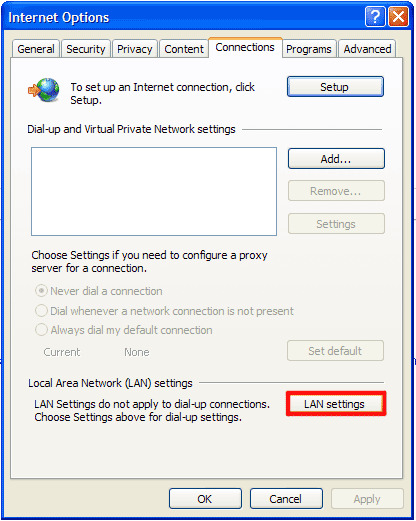
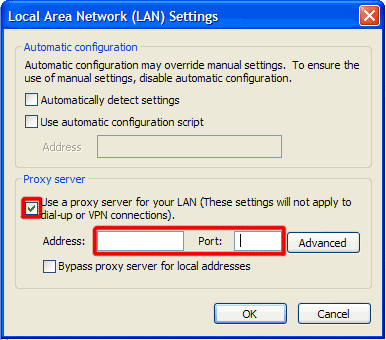
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Recovery Series
| ||||||||

|
How to manually remove Windows Recovery Series
Files associated with infection (Windows Recovery Series):
%CommonStartMenu%\Programs\Windows Antivirus Care.lnk
%AppData%\result.db
%AppData%\Protector-[Random].exe
%AppData%\NPSWF32.dll
Dynamic Link Libraries to remove (Windows Recovery Series):
Processes to kill (Windows Recovery Series):
Remove registry entries (Windows Recovery Series):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utpost.exe

Post comment — WE NEED YOUR OPINION!