- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Normal system programs crash immediatelly
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Windows Protection UnitWindows Protection Unit is a counterfeit computer security application which will make you think that your computer’s system is just about to be damaged. You will notice that because Windows Protection Unit will display such information that you might decide to do whatever it takes to protect the system. Windows Protection Unit should not be trusted but deleted from the system, and if you want to know why, keep on reading the article. Windows Protection Unit was created to deceive unfortunate Windows users by tricking them into believing that the system is infected. Windows Protection Unit frightens users insolently with imaginary threats and simulated pop-ups in the task bar. It might also block access to the Internet or hide some icons from the desktop so that users would think that there is no way to solve the problems. However, Windows Protection Unit will offer its support and direct you to buy its full version which is imaginary. Ignorance of the suggestion and removal of Windows Protection Unit is the best way to protect your money and financial information, because these two things are what cyber criminals actually care about. What you should care about is how to remove of Windows Protection Unit. It may seem to you that it is easy, but it is not. When deleting Windows Protection Unit manually, you have to get rid of a bunch of files and dispose of modified Registry entries, as the rogue makes some changes in the system in order to stay in it for as long time as possible. To ease up the process of removal, we suggest using a legitimate antispyware application which deletes the rogue automatically, and you do not have to worry about manual system’s changes. UPDATEIt has been found out that Windows Protection Unit is the replica of such fake Rogue.VirusDoctor family antispywares as Windows Foolproof Protection, Windows Component Protector or Windows Cleaning Tools, all of which we have already showed you how to remove from your PCs. Just like previous rogues, Windows Protection Unit also presents disabilities to connect to the Internet, run most executable files or access Registry Editor and Task Manager, all of which are implemented to guard Windows Protection Unit against being detected and removed swiftly. Alongside these symptoms, Windows Protection Unit also proclaims such misinforming notifications, as listed bellow: Error Error Error Recommended: To remove all of these symptoms and restore Windows component’s functionality, use this registration key: 0W000-000B0-00T00-E0020. Note that this action will not delete Windows Protection Unit from your computer!
Download Spyware Removal Tool to Remove* Windows Protection Unit
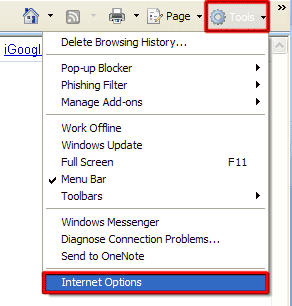
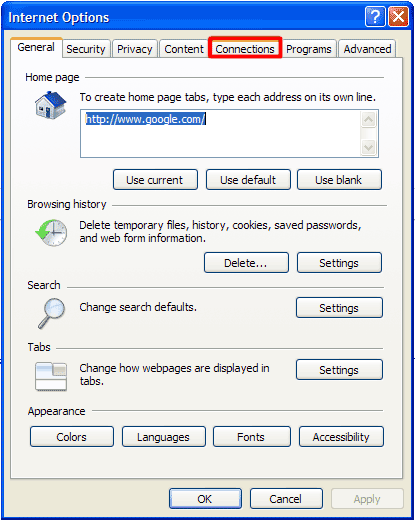
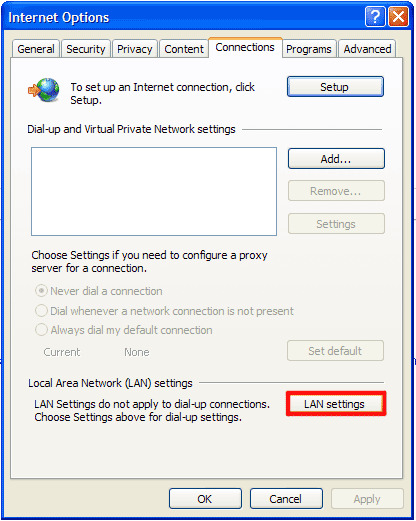
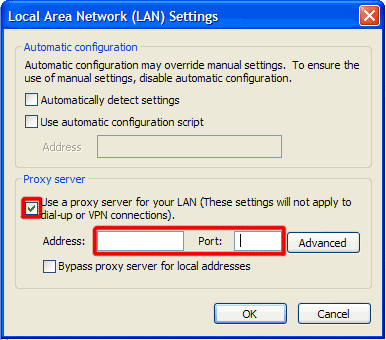
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Protection Unit
| ||||||||

|
How to manually remove Windows Protection Unit
Files associated with infection (Windows Protection Unit):
%AppData%\NPSWF32.dll
%AppData%\Protector-[Random].exe
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Protection Unit.lnk
%Desktop%\Windows Protection Unit.lnk
Dynamic Link Libraries to remove (Windows Protection Unit):
Processes to kill (Windows Protection Unit):
Remove registry entries (Windows Protection Unit):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "okanrqfdwk"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\atro55en.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bisp.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\esafe.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\install[4].exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mssmmc32.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pcip10117_0.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scrscan.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utpost.exe

Post comment — WE NEED YOUR OPINION!