- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Normal system programs crash immediatelly
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
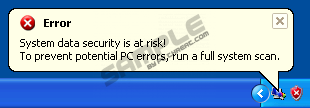
Windows Managing SystemThere is not a single day that a computer would not get infected by a rogue antispyware application. Windows Managing System is one of them, and it sure wants to find its way into your computer no matter what. If you already have this rogue in your system then this article is for you. The first thing you have to know about Windows Managing System is that it is NOT an antivirus program, even though it claims to be one. It might be hard to believe otherwise, because Windows Managing System has a nice user interface and all of its messages seem to be part of the Windows operating system’s security, but that is definitely not true. Windows Managing System is there in your computer, because it wants your money. Even though it cannot get into your wallet directly, it has many ways to lure your hard-earned money out of you. If you don’t want to be robbed, you mustn’t open the Windows Managing System purchase page and pay for the full version of the program. If you do, your credit card information will be revealed to a third party and they will be able to illegally access your bank account. Do not become yet another victim of this rogue. Protect your money and your computer from this threat by removing Windows Managing System from your computer for good using a reliable security tool. UPDATE If you are wondering where Windows Managing System comes from, it belongs to the Rogue.VirusDoctor family, and some of its previous versions include Windows Trojans Sleuth, Windows Firewall Constructor, Windows Safety Tweaker. Due to its notorious background Windows Managing System is a dangerous rogue antispyware, able to convince you that your computer is infected with various malware. Upon the infection Windows Managing System performs a fake system scan and "finds" a number of viruses in your computer. It goes as far as giving the names and descriptions of these infections, for example: Virus name: Email-Flooder If that weren’t enough, Windows Managing System also spams you with fake security notifications that pop up every now and then: Error Warning If you want to get rid of Windows Managing System, you MUST NOT pay for the program. Be reasonable and protect your financial funds from the cyber criminals who have created the rogue. A way to win against this rogue is to use this activation key to “register” Windows Managing System: 0W000-000B0-00T00-E0020 After the “activation” the rogue will calm down, and you will have time to erase Windows Managing System for good. Just don’t wait until the second wave of assault comes and if you cannot terminate Windows Managing System on your own, do it with a reliable computer security program. | ||||||||
|
Download Spyware Removal Tool to Remove*
Windows Managing System
| ||||||||

|
How to manually remove Windows Managing System
Files associated with infection (Windows Managing System):
%AppData%\Protector-[Random].exe
%AppData%\result.db
%CommonStartMenu%\Programs\Windows Managing System.lnk
%Desktop%\Windows Managing System.lnk
Dynamic Link Libraries to remove (Windows Managing System):
Processes to kill (Windows Managing System):
Remove registry entries (Windows Managing System):
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = 2012-3-5_1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirus.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autoupdate.exe

Post comment — WE NEED YOUR OPINION!