- Blocks internet connection
- Block exe files from running
- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Internet Security 2012Never believe anything Internet Security 2012 has to say. This rubbish rogue antispyware application was designed with the express intention of fleecing PC owners out of their money while leaving them with nothing of value in return. Internet Security 2012 will enter the system surreptitiously and remain hidden from the user until it is ready to start its attack. It will use any nefarious tactic at its disposal to facilitate its surreptitious infiltration of the system.
Download Spyware Removal Tool to Remove* Internet Security 2012
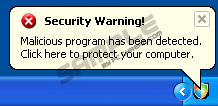
The user will only become aware of Internet Security 2012’s presence once the rogue starts its attack by generating a fake security scan of the system. This fake scan will yield many bogus security threats as being present on the system. Shortly following this the false security scan the user will find him spammed with falsely generated security messages informing him of the same thing. These fake security messages should not be trusted. Users will also find that they are suddenly unable to connect to the Internet and will not be able to launch applications on the infected PC. Get rid of Internet Security 2012 and protect your PC against this seditious rogue antispyware. UPDATEThe latest research on the rogueware has revealed more information on it. Being a clone of Privacy Protection, Internet Security 2012 is installed using the rootkit technique – the parasite is hidden in the system in a way that it would be difficult to detect it. However, the executable file of the malware isecurity.exe which is detected as Trojan.Agent/Gen-FakePrivacy by most antivirus software is installed on the location %CommonAppData%\isecurity.exe. For a legitimate application, this file location is uncommon. In addition, isecurity.exe starts automatically from Run, RunOnce, RunServices, or RunServicesOnce entry in the registry. Thus, Internet Security 2012 has made lots of changes on the system when the infection has reached its target. After the inner parts of the system have been modified, the user will notice different kinds of warnings displayed on the screen. Most of them will be related to the messages on damaged computer safety: Windows Security Center reports that Internet Security 2012 is enable. Internet Security 2012helps to protect your computer against viruses and other security threats. Click Recommendations for the suggested actions. Your system might be at risk now. Spyware alarm! Trojan detected! WARNING! Internet Security 2012 has found [random number] useless and UNWANTED files on your computer! In addition, you won’t be able to execute most of the programs installed as the following message will pop up: [file name] can not start Unfortunately, these are not the only changes made on the system. As soon as Internet Security 2012 gets into the system, you will notice that your computer started to act weirdly: the machine works slower, you are connected to the internet and redirected to the malicious websites whenever you try to open some website, even the results of Google or Yahoo search are modified according to the wishes of the hackers. Besides, sometimes after the performance of your computer slowed down, it even might happen that the system freezes totally and you can’t open TaskManager, get into the Registry, access other parts of the system, or even open most of the programs, including your antivirus software. All in all, there is a way out of this trouble. You have to remove Internet Security 2012 as soon as possible. According to the latest information, you should first register this malware and, only then, remove it. In the registration form of Internet Security 2012, enter one of the following activation keys: Y76REW-T65FD5-U7VBF5A Y86REW-T75FD5-U9VBF4A You won’t see the warning messages any more. In addition, you will be able to run your antivirus software which was previously blocked by Internet Security 2012. After registering the fake application, remove the files listed below. In case you are not sure how to do that, be sure to use a legitimate antimalware tool which will do everything for you. UPDATEDue to the fact that Internet Security 2012 blocks all executable files, it might be challenging to get rid of the rogue even after you have entered the activation key. No one knows exactly when Internet Security 2012 will spring back into action again, so you have to be swift about it. If you choose automatic removal instead of the manual one, you might encounter difficulties in attaining a security program of choice. Here’s how you go around the rogue’s defenses: when Internet Security 2012 offers to remove the non-existent threats, press the “Yes, activate Internet Security 2012 now” button, and you will see the fake activation page being loaded. This way you open the internet browser even though technically Internet Security 2012 should not allow you that. When the page loads, press Ctrl+N and a new browser wind will show up, allowing you to roam internet freely again. This is when you have to acquire the legitimate computer safety program and remove Internet Security 2012 for good. Or you can turn on a totally clean computer and download a computer safety program there. Later on, transfer it onto your computer with a USB flash drive, for example, and get rid of Internet Security 2012 at once. | ||||||||
|
Download Spyware Removal Tool to Remove*
Internet Security 2012
| ||||||||

|
How to manually remove Internet Security 2012
Files associated with infection (Internet Security 2012):
%UserProfile%\.Internet Security 2012
%CommonPrograms%\Internet Security 2012\Internet Security 2012.lnk
Processes to kill (Internet Security 2012):
Remove registry entries (Internet Security 2012):
HKEY_CURRENT_USER\Software\Microsoft\Installer\Products\random
HKEY_LOCAL_MACHINE\Software\Internet Security 2012.exe
HLEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “random”

Post comment — WE NEED YOUR OPINION!