- Installs itself without permissions
- Connects to the internet without permission
- Slow internet connection
- System crashes
- Annoying Pop-up's
- Slow Computer
Personal Security SentinelDevelopers of rogue antispyware applications such as Personal Security Sentinel have no squabbles about sinking to the lowest depths of depravity in their campaign to defraud honest consumers who care about their systems’ security out of their hard earned money. This is proven by the vitriolic intensity behind the attack of Personal Security Sentinel, which hails from the FakeVimes family of rogues which includes the likes of Internet Security Suite and Internet Antivirus 2011. It is obvious from the company this rogue keeps that users infected with it will need to get rid of Personal Security Sentinel if they value the safety and health of their systems. Following the same route of attack as most other rogue antispyware applications, Personal Security Sentinel will start its attack off on the PC by falsely informing the user that his PC is under attack from various harmful Internet viruses. This falls in line with Personal Security Sentinel’s attack on the system as it aims to create panic in the user, afterwards offering him a seemingly easy and legitimate solution to his troubles. If the user does not go on to pay for a licensed copy of Personal Security Sentinel, this rogue will cripple the system and render it ultimately unusable and utterly useless. Users who did not delete Personal Security Sentinel in time have reported on various distressing symptoms, which include being denied access to their Desktop items, being unable to connect to the Internet and ultimately an utterly slowed down system. Do not take chances with Personal Security Sentinel, and do not become its next victim. Eradicate Personal Security Sentinel from your system by making use of the removal power of a genuine and powerful security application. This will not only effectively and permanently destroy Personal Security Sentinel, but will offer future protection against similar threats.
Download Spyware Removal Tool to Remove* Personal Security Sentinel
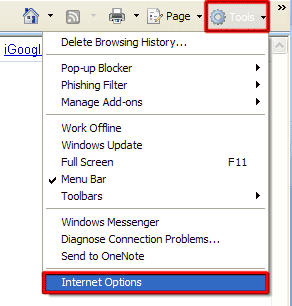
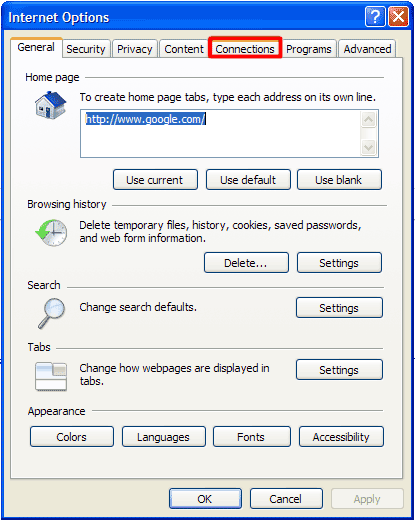
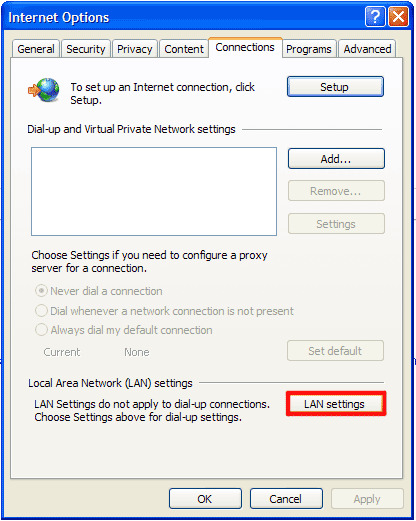
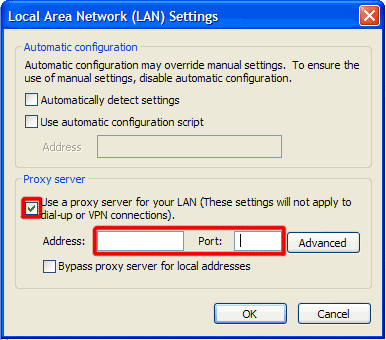
How to renew your internet connection:This rogue antispyware blocks your Internet connection to prevent you from removing the rogue application. To enable the Internet connection, please follow these instructions:
| ||||||||
|
Download Spyware Removal Tool to Remove*
Personal Security Sentinel
| ||||||||

|
How to manually remove Personal Security Sentinel
Files associated with infection (Personal Security Sentinel):
PersonalSS.exe
%UserProfile%\Start Menu\Programs\Personal Security Sentinel.lnk
%UserProfile%\Start Menu\Personal Security Sentinel.lnk
%UserProfile%\Desktop\PersonalSS.exe.txt
%UserProfile%\Desktop\Personal Security Sentinel.lnk
%UserProfile%\Application Data\Personal Security Sentinel\cookies.sqlite
%UserProfile%\Application Data\Personal Security Sentinel\
%UserProfile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Personal Security Sentinel.lnk
c:\Documents and Settings\All Users\Application Data\PSZJLXVS\PSLFNABES.cfg
c:\Documents and Settings\All Users\Application Data\PSZJLXVS\
c:\Documents and Settings\All Users\Application Data\095a\Quarantine Items\
c:\Documents and Settings\All Users\Application Data\095a\PSSSys\
c:\Documents and Settings\All Users\Application Data\095a\unins000.dat
c:\Documents and Settings\All Users\Application Data\095a\sqlite3.dll
c:\Documents and Settings\All Users\Application Data\095a\PSS.ico
c:\Documents and Settings\All Users\Application Data\095a\PersonalSS.exe
c:\Documents and Settings\All Users\Application Data\095a\mozcrt19.dll
c:\Documents and Settings\All Users\Application Data\095a\80e9877130a15854a99bf6dd8d368239.ocx
c:\Documents and Settings\All Users\Application Data\095a\713.mof
c:\Documents and Settings\All Users\Application Data\095a\
Dynamic Link Libraries to remove (Personal Security Sentinel):
sqlite3.dll
Processes to kill (Personal Security Sentinel):
Remove registry entries (Personal Security Sentinel):
HKEY_CLASSES_ROOT\PersonalSS.DocHostUIHandler
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyServer" = "http=127.0.0.1:25553"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Personal Security Sentinel"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Anti-Virus Professional.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntispywarXP2009.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPro_2010.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirusxppro2009.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntiVirus_Pro.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\av360.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brastk.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Cl.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csc.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dop.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\frmwrk32.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gav.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbn976rl.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\homeav2010.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\init32.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MalwareRemoval.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ozn695m5.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pav.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pc.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsAuxs.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsGui.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsSvc.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsTray.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PC_Antispyware2010.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pdfndr.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PerAvir.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qh.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Quick Heal.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QuickHealCleaner.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SafetyKeeper.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Save.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveArmor.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveDefense.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveKeep.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secure Veteran.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\secureveteran.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Security Center.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SecurityFighter.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\securitysoldier.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smart.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smartprotector.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smrtdefp.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SoftSafeness.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spywarexpguard.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrustWarrior.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsc.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\W3asbas.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winav.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windll32.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windows Police Pro.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xpdeluxe.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~1.exe "Debugger" = "svchost.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~2.exe "Debugger" = "svchost.exe"

Comments
This is a brilliant article - very well written and informative. I had all my days with this cursed rogue.
i need trial key
thanh,
try this - UEPB-H4KA-S2LA-U2FD
I REALLY NEED helpy on this i CANNOT find the files and the POS malware is still on my computer please help.